Tuesday, April 30, 2013
 4:19 AM
4:19 AM SL4ID3R
SL4ID3R No comments
No comments
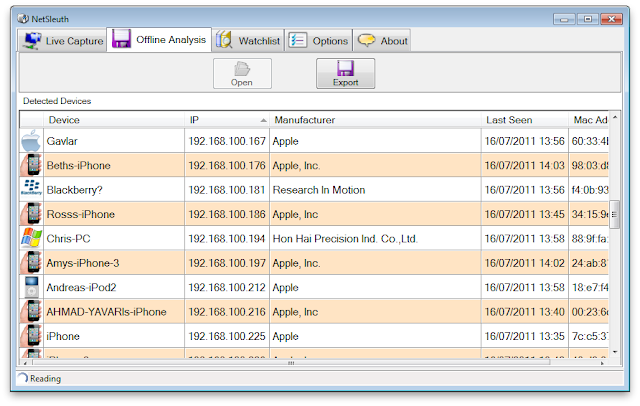
NetSleuth identifies and fingerprints network devices by silent network monitoring or by processing data from PCAP files.
NetSleuth is an opensource network forensics and analysis tool, designed for triage in incident response situations. It can identify and fingerprint network hosts and devices from pcap files captured from Ethernet or WiFi data (from tools like Kismet).
NetSleuth is an opensource network forensics and analysis tool, designed for triage in incident response situations. It can identify and fingerprint network hosts and devices from pcap files captured from Ethernet or WiFi data (from tools like Kismet).
It also includes a live mode, silently identifying hosts and devices without needing to send any packets or put the network adapters into promiscuous mode ("silent portscanning").
NetSleuth is a free network monitoring, cyber security and network forensics analysis (NFAT) tool that provides the following features:
- An easy realtime overview of what devices and what people are connected to any WiFi or Ethernet network.
- Free. The tool can be downloaded for free, and the source code is available under the GPL.
- Simple and cost effective. No requirement for hardware or reconfiguration of networks.
- “Silent portscanning” and undetectable network monitoring on WiFi and wired networks.
- Automatic identification of a vast array of device types, including smartphones, tablets, gaming consoles, printers, routers, desktops and more.
- Offline analysis of pcap files, from tools like Kismet or tcpdump, to aid in intrusion response and network forensics.
 4:17 AM
4:17 AM SL4ID3R
SL4ID3R No comments
No comments
Phrozen Keylogger Lite is finally available, developed by Dark comet RAT developer. Phrozen Keylogger Lite is a powerful and user friendly keylogger especially created for Microsoft Windows systems. Phrozen Keylogger Lite is compatible with all currently supported versions of Windows, which effectively means Windows XP to the recently released Windows 8.
Phrozen Keylogger Lite has been especially created to capture all keystrokes from any type of keyboard (PS/2, USB and even Virtual Keyboards). The captured keystrokes are stored into a local database. There they are sorted by their process name and the active window into a log.
Phrozen Keylogger Lite is running silently in background. When the program is successfully installed on a computer, it will capture all keystrokes fully stealthily and the program will remain hidden from every user. It will not slow down the computer it is installed on.
If you want to consult the logs of the current day or previous days just press the so-called “Magic Shortcut” and enter your personal password and the logs will be made visible in a new window. You can easily manage, export, delete, mark as important, mail, etc. these logs.
Phrozen Keylogger Lite also gives you the possibility to manage black listed words. When such a word is entered via keystrokes you will immediately be sent a mail which contains the entire context in which that ‘black listed word’ appears. This is a very useful feature: suppose you have forbidden your son to go to a specific gambling site and he does go there against your wishes, you then immediately get a mail that warns you of this transgression.
Download Phrozen Keylogger Lite v1.0
 4:16 AM
4:16 AM SL4ID3R
SL4ID3R No comments
No comments
One of the biggest and very comprehensive collection of 1,493,677,782 word for Password cracking list released for download. The wordlists are intended primarily for use with password crackers such as hashcat, John the Ripper and with password recovery utilities.

Defuse Security have released the wordlist of 4.2 GiB (compressed) or 15 GiB (uncompressed) used by their Crackstation project.
Wordlist originally shared by 'Stun', Anonymous Hacktivist. You can also download it from Torrent.
Subscribe to our Daily Newsletter via email - Be First to know about Security and Penetration testing tools. or Join our HugeHackers Community on Facebook , Google+ and Twitter .

Defuse Security have released the wordlist of 4.2 GiB (compressed) or 15 GiB (uncompressed) used by their Crackstation project.
Wordlist originally shared by 'Stun', Anonymous Hacktivist. You can also download it from Torrent.
Subscribe to our Daily Newsletter via email - Be First to know about Security and Penetration testing tools. or Join our HugeHackers Community on Facebook , Google+ and Twitter .
 4:14 AM
4:14 AM SL4ID3R
SL4ID3R No comments
No comments
 The Social-Engineer Toolkit (SET) version 4.7 codename “Headshot” has been released. This version of SET introduces the ability to specify multi-powershell injection which allows you to specify as many ports as you want and SET will automatically injectPowerShell onto the system on all of the reverse ports outbound. What’s nice with this technique is it never touches disk and also uses already white listed processes. So it should never trigger anything like anti-virus or whitelisting/blacklisting tools. In addition to multi-powershell injector, there are a total of 30 new features and a large rewrite of how SET handles passing information within different modules.
The Social-Engineer Toolkit (SET) version 4.7 codename “Headshot” has been released. This version of SET introduces the ability to specify multi-powershell injection which allows you to specify as many ports as you want and SET will automatically injectPowerShell onto the system on all of the reverse ports outbound. What’s nice with this technique is it never touches disk and also uses already white listed processes. So it should never trigger anything like anti-virus or whitelisting/blacklisting tools. In addition to multi-powershell injector, there are a total of 30 new features and a large rewrite of how SET handles passing information within different modules.Change log for version 4.7
removed a prompt that would come up when using the powershell injection technique, port.options is now written in prep.py versus a second prompt with information that was already provided
began an extremely large project of centralizing the SET config file by moving all of the options to the set.options file under src/program_junk
moved all port.options to the central routine file set.options
moved all ipaddr.file to the central routine file set.options
changed spacing on when launching the SET web server
changed the wording to reflect what operating systems this was tested on versus browsers
removed an un-needed print option1 within smtp_web that was reflecting a message back to user
added the updated java bean jmx exploit that was updated in Metasploit
added ability to specify a username list for the SQL brute forcing, can either specify sa, other usernames, or a filename with usernames in it
added new feature called multi-powershell-injection – configurable in the set config options, allows you to use powershell to do multiple injection points and ports. Useful in egress situations where you don’t know which port will be allowed outbound.
enabled multi-pyinjection through java applet attack vector, it is configured through set config
removed check for static powershell commands, will load regardless – if not installed user will not know regardless – better if path variables aren’t the same
fixed a bug that would cause linux and osx payloads to be selected even when disabled
fixed a bug that would cause the meta_config file to be empty if selecting powershell injection
added automatic check for Kali Linux to detect the default moved Metasploit path
removed a tail comma from the new multi injector which was causing it to error out
added new core routine check_ports(filename, ports) which will do a compare to see if a file already contains a metasploit LPORT (removes duplicates)
added new check to remove duplicates into multi powershell injection
made the new powershell injection technique compliant with the multi pyinjector – both payloads work together now
added encrypted and obfsucated jar files to SET, will automatically push new repos to git everyday.
rewrote the java jar file to handle multiple powershell alphanumeric shellcode points injected into applet.
added signed and unsigned jar files to the java applet attack vector
removed create_payload.py from saving files in src/html and instead in the proper folders src/program_junk
fixed a payload duplication issue in create_payload.py, will now check to see if port is there
removed a pefile check unless backdoored executable is in use
turned digital signature stealing from a pefile to off in the set_config file
converted all src/html/msf.exe to src/program_junk/ and fixed an issue where the applet would not load properly
It can also be downloaded through github using the following command:
git clone https://github.com/trustedsec/social-engineer-toolkit/ set/
Saturday, April 27, 2013
 5:26 AM
5:26 AM SL4ID3R
SL4ID3R No comments
No comments
hello guys this is an ultimate hacking tool just like the hc stealer but more efficient than it-
here is the dowload link
DOWNLOAD FROM HERE
DOWNLOAD THE TUTORIAL FROM HERE
here is the dowload link
DOWNLOAD FROM HERE
DOWNLOAD THE TUTORIAL FROM HERE
 5:19 AM
5:19 AM SL4ID3R
SL4ID3R No comments
No comments
This Tutorial is for education purposes ONLY and I am NOT responsible in any way on how you use the information provided and what you do with the files.
Thank you and enjoy reading.
First of all I want to tell you that ZeuS Bot is the most illegal bot out there. It is a bot that connects to a HTTP webhost and not to a IRC channel or a PC. It is highly illegal as it is considered as a banking trojan as it logs every internet activity to a database. Well lets sta rt.
Step 1:
First of all you need offshore hosting, preferably bulletproof. The best i've found so far is SANTREX and VieFireHosting.
For VieFireHosting use this coupon provided by Nima304 which will get you a 50% Discount
Coupon Code:
X234A
Sign up, preferably with a domain. Think of a domain that is not easily tracked though if possible.
After that get the files needed. The files come with a black instead of blue theme, I editted the .css myself because I was bored.

Step 2:
Uploading the files.
1. Go and login into your CPanel X.

2. Go to File Manager.

3. Go and create a directory of your choice.

4. Upload the upload.zip to the directory created.

5. After that extract the files.

6. Chmod the directory /install/ and /system/ to 777. Also the whole directory.

Step 3:
Creating the Database.
1. Go to MySQL Databases in your CPanel.

2. Create a database and write the name down.

3. Add new user and write the details down.

4. Now add the created user to the created database. Be sure to select all privileges.


5. Be sure you have written everything down and move to the next step.
Step 4:
Installing the panel.
1. Navigate to the directory you created and got to /directory/install/. A Panel installer should appear.

2. What to enter:
Username: Enter the default username which you will use when logging in.
Password: Your password when logging in. Make it strong.
MySQL server:
Host: "localhost"
User: Your database user created before.
Password: Your database password created for the user.
Database: The database name.
Online bot timeout: Leave it as it is.
Encryption key use something VERY strong.
Then Click Install.

Step 5:
Making the bot.
1. Navigate to your ZeuS files and open config.txt
Replace the link where it says with your link. Also the encryption key you used before.

2. Open the zsb.exe
The builder also has a remover so if you test your server on your own pc you can just remove it with a mouse click.
Click on Builder.

Then click on Build Config. Save the file.
Click Build Loader. Save the file.




Now go and upload cfg.bin and bt.exe to the same directory as the panel.
Also you can delete the /install/ folder since the panel has been installed in the previous step.

In final the directory with Zeus installed should look like this:

Installed! Now a tutorial on how everything works!
Now navigate to the directory where you hav your ZeuS bot panel. Got to /directory/cp.php
A login box like this should be there:

Enter your panel username and password.
if you would like for your browser to keep cookies so that you don't need to login again every time you leave the page check the option.
Click Submit.

So now here is the panel.

1. Shows you the current user
2. Shows you the summary (see green comments)
3. Shows you the OS statistics of the infected bots.
4. You can browse through the bots and and their reports
5. You can browse through the scripts you got. Add/edit them.
6. There you can search trough the reports in the database
7. There you can search through the reports which are most times is txt format.
8. Just random information about your system and stuff.
10. Options. If you change the encryption key the automatically you loose all your bots. You need to make new server and config file with the new encryption key and spread it again.
11. Change your password.
12. Add and manage users.
1. Shows you the number of total reports in database.
2. Shows you the time the first bot came online.
3. Shows you total bots. The number of total pc's infected.
4. Shows you the number of active bots ins the past 24 hours.
5. Shows you the minimal version of bots.
6. Shows you the maximal version of bots.
7. Installs. Every pc which has not been infected with a Zeus bot server before gets on this list.
8. With this buttons you can reset the installs.
9. Shows you how much bots are currently online.
10. Lets you jump to statistics of a botnet.
Thank you and enjoy reading.
First of all I want to tell you that ZeuS Bot is the most illegal bot out there. It is a bot that connects to a HTTP webhost and not to a IRC channel or a PC. It is highly illegal as it is considered as a banking trojan as it logs every internet activity to a database. Well lets sta rt.
Step 1:
First of all you need offshore hosting, preferably bulletproof. The best i've found so far is SANTREX and VieFireHosting.
For VieFireHosting use this coupon provided by Nima304 which will get you a 50% Discount
Coupon Code:
X234A
Sign up, preferably with a domain. Think of a domain that is not easily tracked though if possible.
After that get the files needed. The files come with a black instead of blue theme, I editted the .css myself because I was bored.
Download Zeus From here
Step 2:
Uploading the files.
1. Go and login into your CPanel X.
2. Go to File Manager.
3. Go and create a directory of your choice.
4. Upload the upload.zip to the directory created.
5. After that extract the files.
6. Chmod the directory /install/ and /system/ to 777. Also the whole directory.
Step 3:
Creating the Database.
1. Go to MySQL Databases in your CPanel.
2. Create a database and write the name down.
3. Add new user and write the details down.
4. Now add the created user to the created database. Be sure to select all privileges.
5. Be sure you have written everything down and move to the next step.
Step 4:
Installing the panel.
1. Navigate to the directory you created and got to /directory/install/. A Panel installer should appear.
2. What to enter:
Username: Enter the default username which you will use when logging in.
Password: Your password when logging in. Make it strong.
MySQL server:
Host: "localhost"
User: Your database user created before.
Password: Your database password created for the user.
Database: The database name.
Online bot timeout: Leave it as it is.
Encryption key use something VERY strong.
Then Click Install.
Step 5:
Making the bot.
1. Navigate to your ZeuS files and open config.txt
Replace the link where it says with your link. Also the encryption key you used before.
2. Open the zsb.exe
The builder also has a remover so if you test your server on your own pc you can just remove it with a mouse click.
Click on Builder.
Then click on Build Config. Save the file.
Click Build Loader. Save the file.
Now go and upload cfg.bin and bt.exe to the same directory as the panel.
Also you can delete the /install/ folder since the panel has been installed in the previous step.
In final the directory with Zeus installed should look like this:
Installed! Now a tutorial on how everything works!
Now navigate to the directory where you hav your ZeuS bot panel. Got to /directory/cp.php
A login box like this should be there:
Enter your panel username and password.
if you would like for your browser to keep cookies so that you don't need to login again every time you leave the page check the option.
Click Submit.
So now here is the panel.
1. Shows you the current user
2. Shows you the summary (see green comments)
3. Shows you the OS statistics of the infected bots.
4. You can browse through the bots and and their reports
5. You can browse through the scripts you got. Add/edit them.
6. There you can search trough the reports in the database
7. There you can search through the reports which are most times is txt format.
8. Just random information about your system and stuff.
10. Options. If you change the encryption key the automatically you loose all your bots. You need to make new server and config file with the new encryption key and spread it again.
11. Change your password.
12. Add and manage users.
1. Shows you the number of total reports in database.
2. Shows you the time the first bot came online.
3. Shows you total bots. The number of total pc's infected.
4. Shows you the number of active bots ins the past 24 hours.
5. Shows you the minimal version of bots.
6. Shows you the maximal version of bots.
7. Installs. Every pc which has not been infected with a Zeus bot server before gets on this list.
8. With this buttons you can reset the installs.
9. Shows you how much bots are currently online.
10. Lets you jump to statistics of a botnet.
Subscribe to:
Posts (Atom)